Problem: [陇剑杯 2021]机密内存(问1)
思路
- 解题大致思路
下载解压得到
一、分析
Encryption.bin01 Encryption.bin02 mem_secret-963a4663.vmem
在Encryption.bin02发现vmware等字眼,初步判断为vmware加密文件
bin01:vmss bin02:vmx(需修复)+vmdk(需修复) vmem:运行状态虚拟机的内存页面文件
二、恢复并破解密码
第一行指定编码格式,第二行是安全密匙(Url 编码的密匙信息+Base64编码的密匙),第三行是Base64编码的加密数据。
分离Encryption.bin02,以1250行0D0A为边界,分离文件为vmx和vmdk
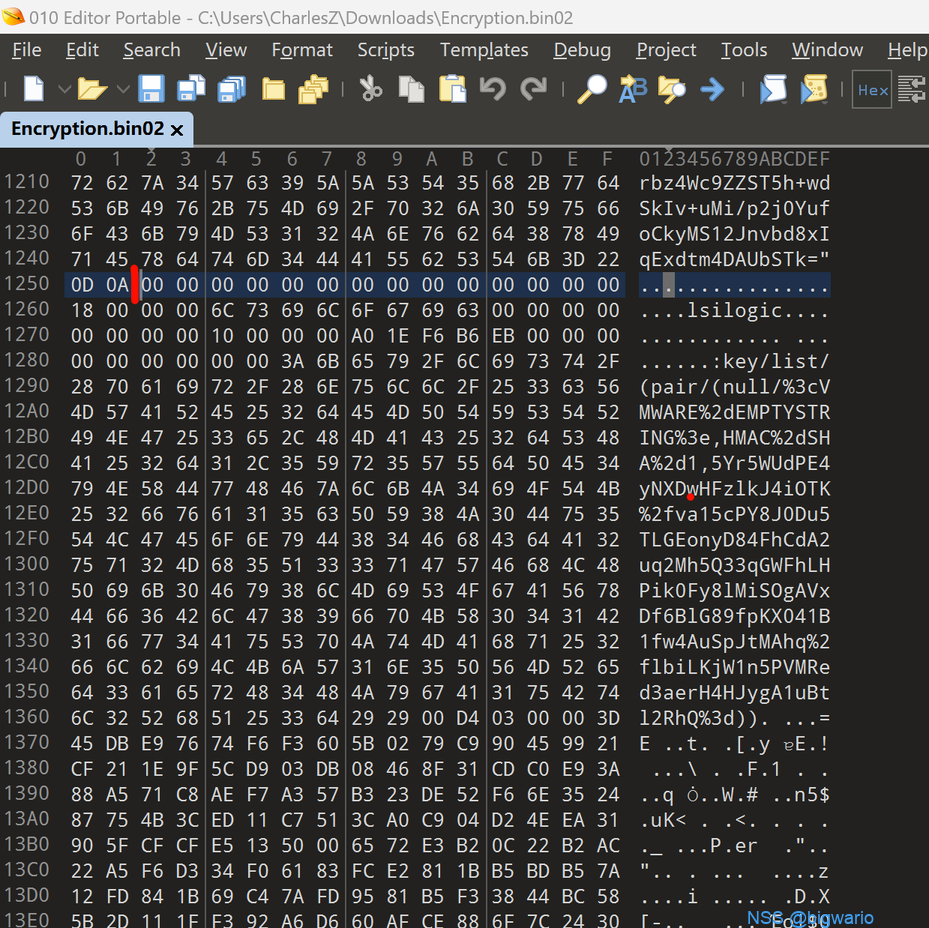
修改vmx文件头,如下
.encoding = "GBK" displayName = "mem_secret" encryption.keySafe = "vmware:key/list/(pair/(phrase/Dg7Se8rqkNI%3d/pass2key%3dPBKDF2%2dHMAC%2dSHA%2d1%3acipher%3dAES%2d256%3arounds%3d10000%3asalt%3d%2b21PdYUqEQd1wdT2AoPEQw%253d%253d,HMAC%2dSHA%2d1,CgKwC5U7lfLjpVohwbpxufC11yU4a0%2byrP08oY0KDDcP1NL%2fRiLojwTz2JnYqm7baAhtgENYUeFUHXwODjSClaJ%2bSRBhKw6UwET6p3AYK8vs4T0cBrvTjYSrs0baLgG7dozcvL5JxA%2fKYJvriz4Mf%2bMmVvE%3d))" encryption.data = "xxx...xxx"(xxx...xxxx为原始内容)
使用pyvmx-cracker.py爆破虚拟机密码
https://github.com/axcheron/pyvmx-cracker
λ python pyvmx-cracker.py -v mem_secret-963a4663.vmx -d wordlist.txt Starting pyvmx-cracker... [*] KeySafe information... ID = 0e0ed27bcaea90d2 Hash = PBKDF2-HMAC-SHA-1 Algorithm = AES-256 Config Hash = HMAC-SHA-1 Salt = fb6d4f75852a110775c1d4f60283c443 [*] Starting bruteforce... 2 password tested... 11 password tested... 15 password tested... 42 password tested... 78 password tested... 114 password tested... 116 password tested... 145 password tested... 155 password tested... 162 password tested... 184 password tested... 191 password tested... 208 password tested... 242 password tested... 300 password tested... 313 password tested... 325 password tested... 368 password tested... 409 password tested... 439 password tested... 449 password tested... 467 password tested... 476 password tested... 497 password tested... 545 password tested... [*] Password Found = 1q2w3e4r
导入vmware虚拟机,输入密码1q2w3e4r看到虚拟机界面
此时查看详情磁盘,由于没有修复vmdk文件会报错,新建一个Workstation 15.x 虚拟机的windows 10 64位光板虚拟机,除了磁盘选择为单个文件,其余全默认,拿到光板的vmdk文件,改名为mem_secret-963a4663.vmdk,直接使用提示密钥错误,用Encryption.bin02中1800的内容替换掉mem_secret-963a4663.vmdk内存,查看提示密钥定位符错误,再去修补vmware:key/list里的vmware
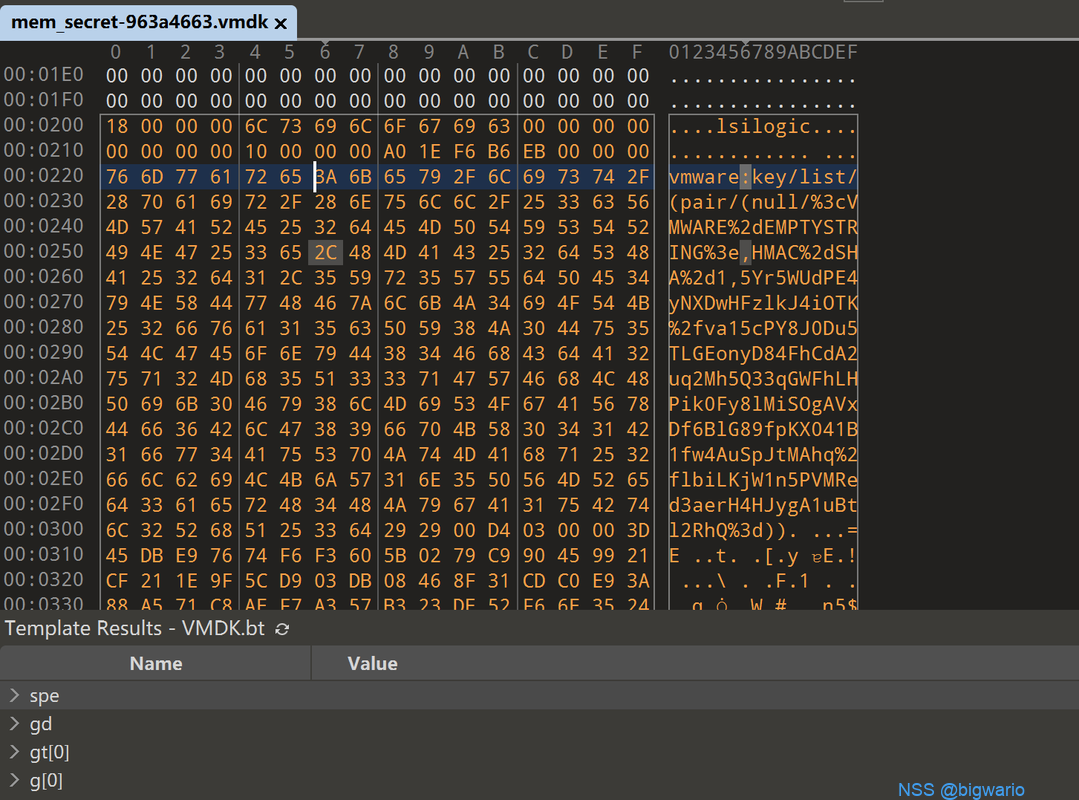
终于可以去掉vmem加密了,使用常用的取证工具开干。
三、收集容器操作系统系统的版本号+容器主机名+系统用户名
Volatility 3 Framework 2.26.0 Variable Value Kernel Base 0xf8005101d000 DTB 0x1ad000 Symbols 1.json.xz Is64Bit True IsPAE False layer_name 0 WindowsIntel32e memory_layer 1 FileLayer KdVersionBlock 0xf800514473c8 Major/Minor 15.18362 MachineType 34404 KeNumberProcessors 2 SystemTime 2021-09-10 16:30:03+00:00 NtSystemRoot C:\Windows NtProductType NtProductWinNt NtMajorVersion 10 NtMinorVersion 0 PE MajorOperatingSystemVersion 10 PE MinorOperatingSystemVersion 0 PE Machine 34404 PE TimeDateStamp Tue Aug 22 00:24:00 1972 Version: 10.0 (build 18363) Computer Name: DESKTOP-4N21ET2 Users: Ado (S-1-5-21-3401425409-1737843151-150623972-1000)
EXP
- 具体攻击代码
总结
- 对该题的考点总结
