Problem: [GHCTF 2025]FishingKit
思路
题目提示了hook
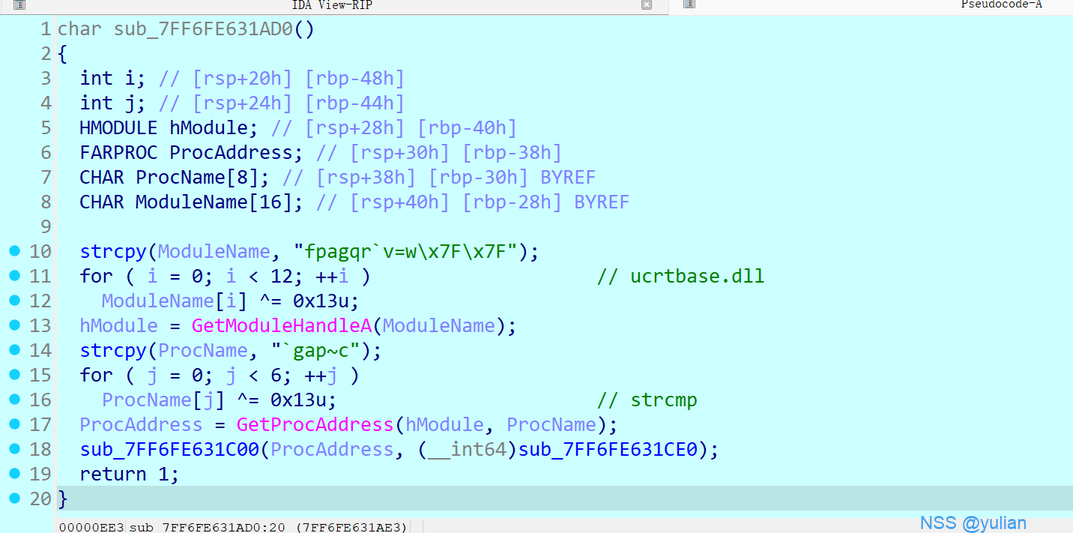
这里是hook函数,将strcmp地址改成了sub_7FF6FE631CE0
查看sub_7FF6FE631CE0函数
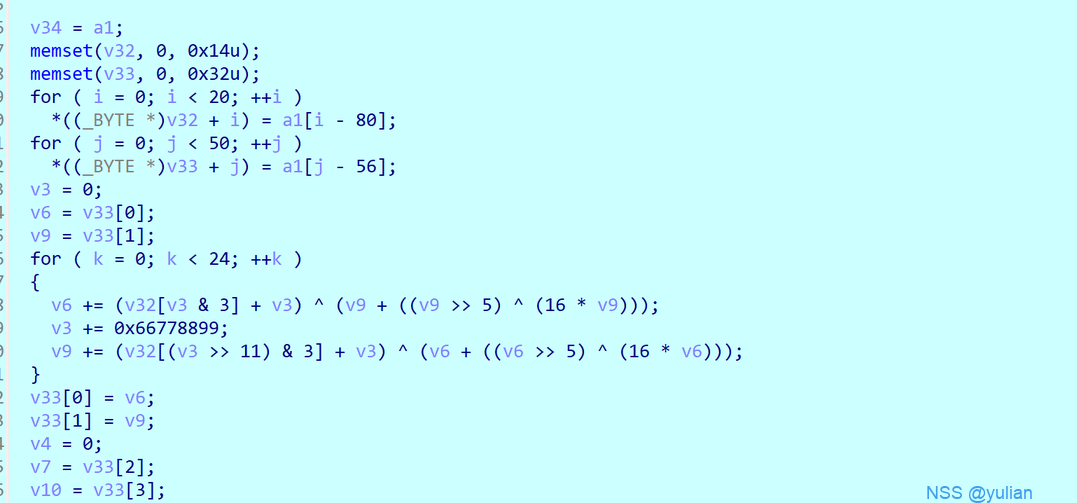
三次xtea,对flag进行加密
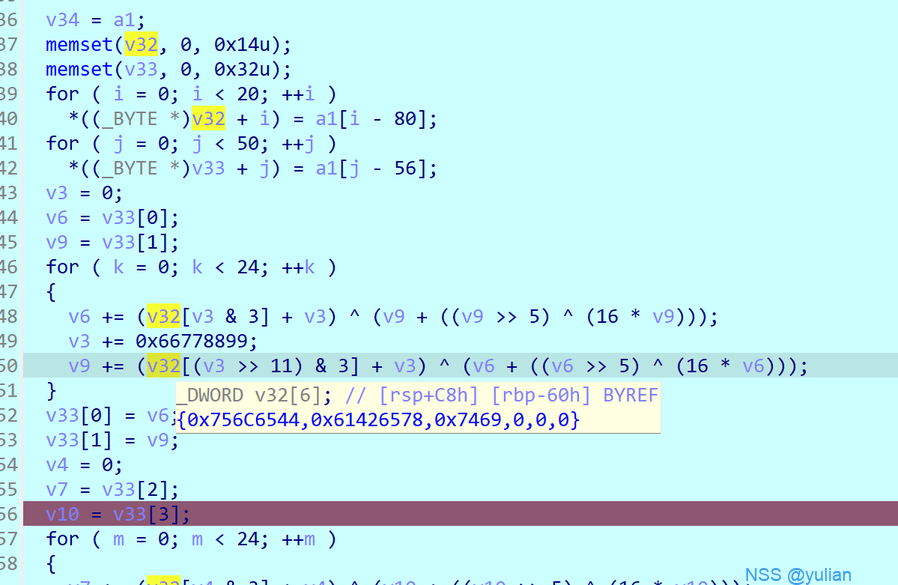
动调发现 key 就是 z3 解出来的 DeluxeBait
密文 byte_7FF6FE6363C8 ,dump一下内存就行
EXP
求key:
from z3 import *
s = Solver()
a = [Int(f'a{i}') for i in range(10)]
for x in a:
s.add(x >= 0, x <= 255)
s.add(202*a[8] + 216*a[5] -17*a[4] -330*a[9] -268*a[6] == -14982)
s.add(325*a[8] +195*a[0] +229*a[1] -530*a[6] -128*a[1] == 22606)
s.add(489*a[1] +480*a[6] +105*a[2] +367*a[3] -135*a[4] -482*a[9] == 63236)
s.add(493*a[1] -80*a[4] -253*a[8] -121*a[2] -177*a[0] -243*a[9] == -39664)
s.add(-352*a[4] +271*a[6] +473*a[7] -72*a[5] == 14255)
s.add(286*a[0] +196*a[7] +483*a[2] +442*a[1] -495*a[8] -351*a[4] == 41171)
s.add(-150*a[2] +283*a[7] -329*a[8] -429*a[9] -261*a[6] == -90284)
s.add(456*a[5] +592*a[7] +92*a[4] -225*a[1] -31*a[2] == 88447)
s.add(221*a[9] +278*a[7] +216*a[6] +237*a[0] +8*a[2] == 83838)
s.add(127*a[9] +121*a[1] +370*a[7] -64*a[4] -422*a[0] == 26467)
s.add(166*a[9] +90*a[1] +262*a[2] +301*a[8] == 88247)
s.add(355*a[0] +282*a[4] +44*a[9] +359*a[8] -167*a[5] -62*a[3] == 76658)
s.add(488*a[6] +379*a[9] -39*a[2] -85*a[1] -277*a[5] == 35398)
s.add(40*a[0] +281*a[4] +217*a[5] -241*a[1] -716*a[7] == -35436)
s.add(870*a[3] +579*a[1] +96*a[8] -133*a[7] == 157448)
if s.check() == sat:
m = s.model()
res = [m[a[i]].as_long() for i in range(10)]
print(''.join(chr(x) for x in res))
解密flag:
#include<stdio.h>
#include<stdint.h>
void decrypt_xtea(uint32_t num_rounds, uint32_t v[2], uint32_t key[4]) {
uint32_t i;
uint32_t v0 = v[0], v1 = v[1], delta = 0x66778899, sum = delta * num_rounds;
for (i = 0; i < num_rounds; i++) {
v1 -= (((v0 << 4) ^ (v0 >> 5)) + v0) ^ (sum + key[(sum >> 11) & 3]);
sum -= delta;
v0 -= (((v1 << 4) ^ (v1 >> 5)) + v1) ^ (sum + key[sum & 3]);
}
v[0] = v0; v[1] = v1;
}
int main()
{
uint8_t enc[] = {
0x21, 0x56, 0x97, 0xA6, 0x1A, 0xD5, 0xC4, 0xDE, 0xA4, 0x9C,
0x82, 0x4D, 0xD1, 0x45, 0xC8, 0x56, 0xA7, 0xB4, 0x96, 0x5C,
0x4D, 0x49, 0x87, 0x20
};
uint32_t key[4] = {0x756C6544,0x61426578,0x7469,0x00000000};
uint32_t tmp[3] = {0x00};
for(int i = 0; i < 3; i++)
{
tmp[0] = *(uint32_t*)(enc + i * 8);
tmp[1] = *(uint32_t*)(enc + i * 8 + 4);
decrypt_xtea(24, tmp, key);
printf("%s",tmp);
}
return 0;
}
